



版权说明:本文档由用户提供并上传,收益归属内容提供方,若内容存在侵权,请进行举报或认领
文档简介
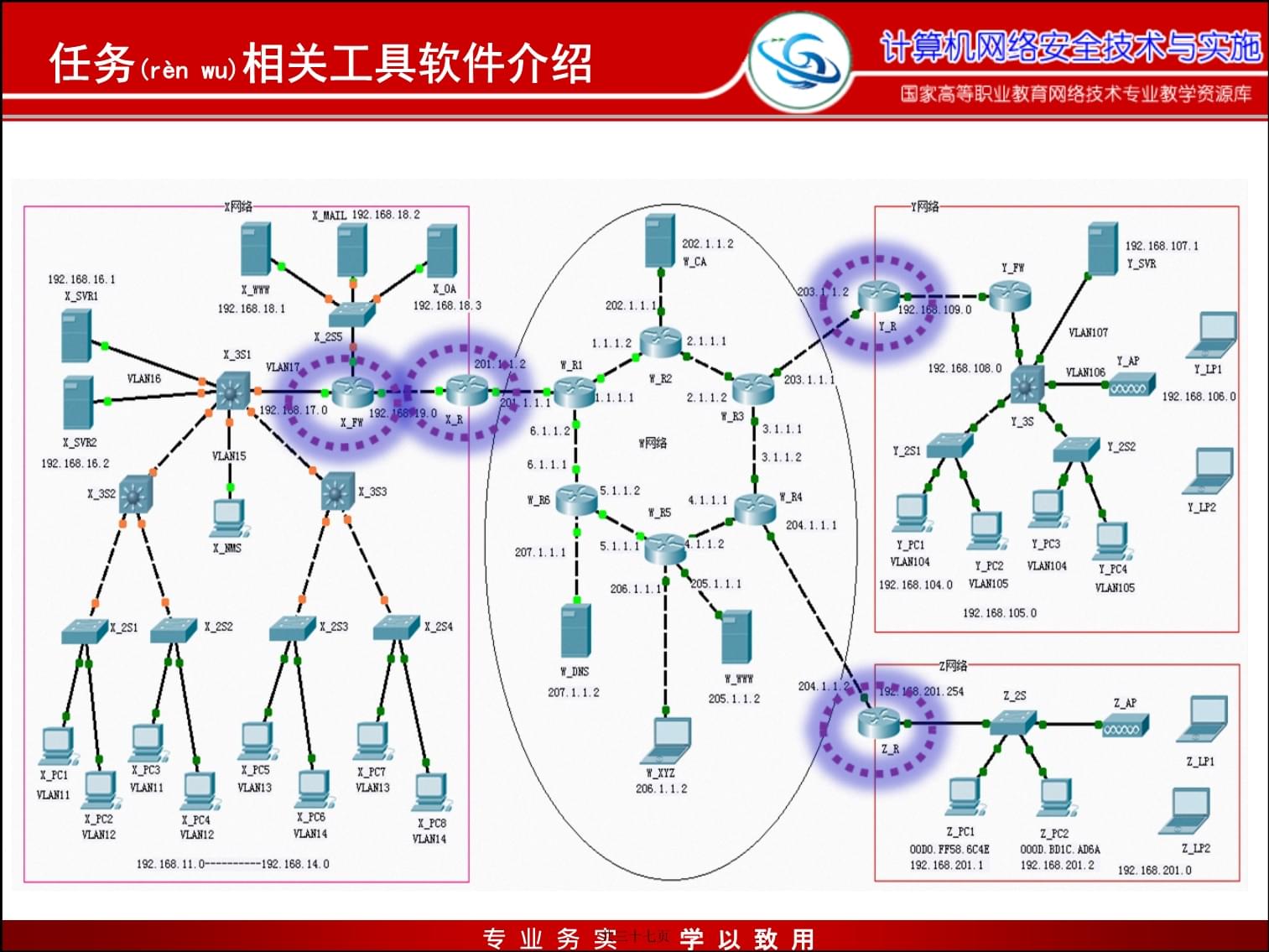
1、计算机网络安全技术(jsh)与实施学习情境4:实训任务4.2基于思科路由器的IOS入侵检测功能(gngnng)配置国家高等职业教育网络技术专业教学资源库共三十七页内容(nirng)介绍任务(rn wu)场景1任务相关工具软件介绍2任务设计、规划3任务实施及方法技巧4任务检查与评价5任务总结6共三十七页任务(rn wu)场景共三十七页任务(rn wu)相关工具软件介绍共三十七页利用命令行对CISCO路由器IOS配置入侵检测(jin c)与防御功能任务设计(shj)、规划共三十七页任务(rn wu)实施及方法技巧 思科12.3(路由器)的第一个版本在2003开始发布,并且不断的在更新一些新的版本,
2、增加了上百个特性,其中之一便是Intrusion Prevention System虽然(surn)从12.0(5)T开始IOS已经支持IDS了,但是当时只支持59个signatures,并且可扩展性也很差。只能算个摆设而已。在 12.3(11)T支持118个signatures。共三十七页任务(rn wu)实施及方法技巧思科IOS IDS/IPS配置:签名定义文件SDF:Signature Definition File SDF定义了它包含的每个签名,当签名被IOS IPS装载以后,IPS立即开始扫描新的签名。默认情况下,IOS里面是不包含任何签名的。下面有三种类型的签名供IOS IPS使用
3、:attack-drop.sdf 83个签名,少于128MB内存的路由器使用。128MB.sdf 300个签名,128或更多的路由器使用。256MB.sdf 500个签名,256或以上的路由器使用。 以上签名都可以用于12.4以后的所有思科接入路由器。如果Flash被清空(qn kn)的话,sdf文件也会被清空。 注意:12.4T-9以后的IOS,不再使用128MB.sdf 而是使用.pkg的文件。 共三十七页任务实施及方法(fngf)技巧思科IOS IDS/IPS配置:IPS配置:pkg版本12.4T-9创建IPS-Signature文件夹 mkdir ips开启IOS IPS特性 ip i
4、ps name iosips acl 配置Signature存储位置存在第一步建立(jinl)的文件夹里面 ip ips config location ips配置警告信息通知 ip ips notify log配置Signature策略 ,对于Signature,必须一开始关闭所有的Signature,然后按照下面的方法开启某些需要的Signature,否则路由器会因内存溢出而崩溃! ip ips signature-category category all retired true共三十七页任务(rn wu)实施及方法技巧思科IOS IDS/IPS配置(pizh):IPS配置:pkg版本
5、12.4T-9开启某一项Signature检测 比如:ios_ips category ios_ips basic retired false exit confirm change y!在接口上启用IPS interface e0/0 ip ips iosips in|out exit加载pkg Signature文件copy t/IOS-S310-CLI.pkg idconf 注意:这里一定要加关键字idconf共三十七页任务实施(shsh)及方法技巧基于CLI配置(pizh)思科路由器IOS的IPS功能共三十七页Cisco IOS IPSCisco IOS IPS enables adm
6、inistrators to manage intrusion prevention on routers that use Cisco IOS Release 12.3(8)T4 or later. Cisco IOS IPS monitors and prevents intrusions by comparing traffic against signatures of known threats and blocking the traffic when a threat is detected. Several steps are necessary to use the Cisc
7、o IOS CLI to work with IOS IPS 5.x format signatures. Cisco IOS version 12.4(10) or earlier used IPS 4.x format signatures and some IPS commands have changed. 共三十七页Download the IOS IPS files:下载IOS的IPS文件Create an IOS IPS configuration directory in flash:在FLASH中建立IPS目录Configure an IOS IPS crypto key:配
8、置验证(ynzhng)特征文件的密钥Enable IOS IPS (consists of several substeps):开启IPS功能Load the IOS IPS signature package to the router:加载特征文件到路由器中Steps to implement Cisco IOS IPS共三十七页1. Download the IOS IPS files. Download the IOS IPS signature file and public crypto key. IOS-Sxxx-CLI.pkg - This is the latest sign
9、ature package.realm-cisco.pub.key.txt - This is the public crypto key used by IOS IPS. The specific IPS files to download vary depending on the current release. Only registered customers can download the package files and key.共三十七页2. Create an IOS IPS directory in FlashCreate a directory in flash to
10、 store the signature files and configurations. Use the mkdir directory-name privileged EXEC command to create the directory. Use the rename current-name new-name command to change the name of the directory. To verify the contents of flash, enter the dir flash: privileged EXEC command. R1# mkdir ipsC
11、reate directory filename ips?Created dir flash:ipsR1#R1# dir flash:Directory of flash:/ 5 -rw- 51054864 Jan 10 2009 15:46:14 -08:00 c2800nm-advipservicesk9-mz.124-20.T1.bin 6 drw- 0 Jan 15 2009 11:36:36 -08:00 ips64016384 bytes total (12693504 bytes free)R1#共三十七页3. Configure an IOS IPS crypto keyCon
12、figure the crypto key to verify the digital signature for the master signature file (sigdef-default.xml). The file is signed by a Cisco to guarantee its authenticity and integrity. To configure the IOS IPS crypto key, open the text file, copy the contents of the file, and paste it in the global conf
13、iguration prompt. The text file issues the various commands to generate the RSA key.共三十七页Highlight and copy the text in the public key file.Paste the copied text at the global config prompt.3. Configure an IOS IPS crypto keyR1# conf tR1(config)#共三十七页Issue the show run command to verify that the key
14、was copied.3. Configure an IOS IPS crypto keyR1# show runcrypto key pubkey-chain rsanamed-key realm-cisco.pub signaturekey-string30820122 300D0609 2A864886 F70D0101 01050003 82010F00 3082010A 0282010100C19E93 A8AF124A D6CC7A24 5097A975 206BE3A2 06FBA13F 6F12CB5B 4E441F1617E630D5 C02AC252 912BE27F 37
15、FDD9C8 11FC7AF7 DCDD81D9 43CDABC3 6007D128B199ABCB D34ED0F9 085FADC1 359C189E F30AF10A C0EFB624 7E0764BF 3E53053E5B2146A9 D7A5EDE3 0298AF03 DED7A5B8 9479039D 20F30663 9AC64B93 C0112A35FE3F0C87 89BCB7BB 994AE74C FA9E481D F65875D6 85EAF974 6D9CC8E3 F0B08B8550437722 FFBE85B9 5E4189FF CC189CB9 69C46F9C
16、A84DFBA5 7A0AF99E AD768C36006CF498 079F88F8 A3B3FB1F 9FB7B3CB 5539E1D1 9693CCBB 551F78D2 892356AE2F56D826 8918EF3C 80CA4F4D 87BFCA3B BFF668E9 689782A5 CF31CB6E B4B094D3F3020301 0001共三十七页3. Configure an IOS IPS crypto keyAt the time of signature compilation, an error message is generated if the publi
17、c crypto key is invalid. If the key is configured incorrectly, the key must be removed and then reconfigured using the no crypto key pubkey-chain rsa and the no named-key realm-cisco.pub signature commands.共三十七页4a. Enable IOS IPSIdentify the IPS rule name and specify the location. Use the ip ips nam
18、e rule name optional ACL command to create a rule name. An optional extended or standard ACL can be used to filter the traffic. Traffic that is denied by the ACL is not inspected by the IPS.Use the ip ips config location flash:directory-name command to configure the IPS signature storage location. P
19、rior to IOS 12.4(11)T, the ip ips sdf location command was used.R1(config)# ip ips name IOSIPSR1(config)# ip ips name ips list ? Numbered access listWORD Named access listR1(config)#R1(config)# ip ips config location flash:ipsR1(config)#共三十七页4b. Enable IOS IPSEnable SDEE and logging event notificati
20、on. The HTTP server must first be enabled using the ip http server command. SDEE notification must be explicitly enabled using the ip ips notify sdee command. IOS IPS also supports logging to send event notification. SDEE and logging can be used independently or simultaneously. Logging notification
21、is enabled by default. Use the ip ips notify log command to enable logging. R1(config)# ip http server R1(config)# ip ips notify sdeeR1(config)# ip ips notify logR1(config)# 共三十七页4c. Configure the Signature CategoryAll signatures are grouped into three common categories:AllBasicAdvancedSignatures th
22、at IOS IPS uses to scan traffic can be retired or unretired. Retired means that IOS IPS does not compile that signature into memory. Unretired instructs the IOS IPS to compile the signature into memory and use it to scan traffic. 共三十七页4c. Configure the Signature CategoryWhen IOS IPS is first configu
23、red, all signatures in the all category should be retired, and then selected signatures should be unretired in a less memory-intensive category. To retire and unretired signatures, first enter IPS category mode using the ip ips signature-category command. Next use the category category-name command
24、to change a category.R1(config)# ip ips signature-categoryR1(config-ips-category)# category allR1(config-ips-category-action)# retired trueR1(config-ips-category-action)# exitR1(config-ips-category)# R1(config-ips-category)# category IOSIPS basicR1(config-ips-category-action)# retired falseR1(config
25、-ips-category-action)# exitR1(config-ips-category)# exitDo you want to accept these changes? confirm yR1(config)#共三十七页4d. Configure the Signature CategoryApply the IPS rule to a desired interface, and specify the direction.Use the ip ips rule-name in | out interface configuration command to apply th
26、e IPS rule. The in argument means that only traffic going into the interface is inspected by IPS. The out argument specifies that only traffic going out of the interface is inspected.R1(config)# interface GigabitEthernet 0/1R1(config-if)# ip ips IOSIPS inR1(config-if)# ip ips IOSIPS outR1(config-if)
27、# exitR1(config)# exit共三十七页5. Load the IOS IPS signatureUpload the signature package to the router using either FTP or TFTP. To copy the downloaded signature package from the FTP server to the router, make sure to use the idconf parameter at the end of the command.copy ftp:/ftp_user:passwordServer_I
28、P_address/signature_package idconfR1# copy ftp:/cisco:cisco/IOS-S376-CLI.pkg idconfLoading IOS-S310-CLI.pkg !OK - 7608873/4096 bytes*Jan 15 16:44:47 PST: %IPS-6-ENGINE_BUILDS_STARTED: 16:44:47 PST Jan 15 2008*Jan 15 16:44:47 PST: %IPS-6-ENGINE_BUILDING: multi-string - 8 signatures - 1 of 13 engines*
29、Jan 15 16:44:47 PST: %IPS-6-ENGINE_READY: multi-string - build time 4 ms - packets for this engine will be scanned*Jan 15 16:44:47 PST: %IPS-6-ENGINE_BUILDING: service-http - 622 signatures - 2 of 13 engines*Jan 15 16:44:53 PST: %IPS-6-ENGINE_READY: service-http - build time 6024 ms - packets for th
30、is engine will be scanned共三十七页5. Load the IOS IPS signatureVerify that the signature package is properly compiled using the show ip ips signature count command.R1# show ip ips signature countCisco SDF release version S310.0 signature package release versionTrend SDF release version V0.0Signature Mic
31、ro-Engine: multi-string: Total Signatures 8multi-string enabled signatures: 8multi-string retired signatures: 8 Signature Micro-Engine: service-msrpc: Total Signatures 25service-msrpc enabled signatures: 25service-msrpc retired signatures: 18service-msrpc compiled signatures: 1service-msrpc inactive
32、 signatures - invalid params: 6Total Signatures: 2136Total Enabled Signatures: 807Total Retired Signatures: 1779Total Compiled Signatures: 351 total compiled signatures for the IOS IPS Basic categoryTotal Signatures with invalid parameters: 6Total Obsoleted Signatures: 11R1#共三十七页任务(rn wu)检查与评价 CLI方式
33、(fngsh)查看IPS配置 R1# show runnning-config | begin ips 检查IPS是否配置正确 R1# show ip ips configuration 检查特征库配置 R1# show ip ips signature 检查IPS接口配置 R1# show ip ips interface 可以用与show相对应的clear命令禁用IPS系统。也可以用debug命令来排错或者检查思科IOS入侵防护系统。 R1# show ip ips all R1# debug ip ips icmp共三十七页任务(rn wu)检查与评价通过本工任务(rn wu)理解网络入
34、侵检测技术与入侵防御的实现过程,这个工作任务(rn wu)建议是由课内完成的,要求达到的目标是:能够区别IDS与IPS技术,正确部署与实施基于思科路由器的入侵防御IPS系统,满足企业网络对入侵防御技术的需求,以最低成本优质完成工作任务,并能进行正确的检查。任务4.2-知识技能要点测评表序号测评要点具体目标测评权重1知识理解对比理解入侵检测技术与入侵防御技术的功能区别,掌握路由器中入侵防御的功能。202工具及软件使用能正确在思科路由器IOS中配置与实施IPS入侵防御功能。103任务实施对CISCO路由器等设备配置IOS入侵检测或防御系统工作任务配置204专业能力提升掌握入侵检测技术及入侵防御技术
35、,通过配置IOS的IPS去深入理解入侵检测及入侵防御技术的工作原理与工作过程205方法能力提升利用学习资源自主进行深入学习206社会能力提升通过小组合作完成任务,提升表达、沟通能力10共三十七页任务(rn wu)总结小结主要介绍了入侵检测技术与入侵防御(fngy)技术相关概念入侵检测技术与入侵防御技术的功能基于思科路由器IOS入侵防御技术的配置与实现练习利用CCP配置思科路由器的IPS功能共三十七页谢谢您的收看(shukn)!请多提宝贵意见!谢谢(xi xie)共三十七页附:配置(pizh)案例任务描述:本任务将基于新的PT图去完成任务,所有设备的网络连通性已经配置完成。本任务是配置R1的IP
36、S,实现对进入内网网络的流量进行描扫检测。内网中一台服务器作为Syslog Server用于记录IPS日志消息。要配置路由器R1识别到日志服务器以便其接收到日志消息。当用日志功能来监控网络时,需要查看一下(yxi)日志消息中的时间和日期是否正确。可以为路由器的日志功能设置CLOCK并配置时间戳服务。最后开启IPS来生成一个在线的ICMP的ECHO应答包的ALERT和DROP动作。共三十七页利用命令行对CISCO路由器IOS配置(pizh)入侵检测与防御功能附:配置(pizh)案例共三十七页附:配置(pizh)案例任务1:使能IOS的IPS功能注意:在PT里,路由器已经把signature文件导
37、入到位了,这些(zhxi)文件默认为存入在FLASH中的xml文件。所以,这里不需要再配置公钥和手动导入signature文件了(如果是在真实设备中没有此文件,可以通过TFTP等方式上传上去)。第一步:检查网络连通性从PC-C去Ping到PC-A应该是成功连通的从PC-A去Ping到PC-C应该是成功连通的第二步:在FLASH中创建一个IOS的IPS配置目录在R1上用MKDIR命令在FLASH内创建目录,目录名为“ipsdir”R1#mkdir ipsdirCreate directory filename ipsdir? Created dir flash:ipsdir第三步:配置IPS的s
38、ignature存放位置在R1上,配置IPS的signature存放位置为上一步创建的目录R1(config)#ip ips config location flash:ipsdir共三十七页附:配置(pizh)案例第四步:建立一条IPS rule,即IPS的检测规则在R1上,配置IPS的rule为在全局下用ip ips name iosips。其中IPS的规则名为iosipsR1(config)# ip ips name iosips第五步:开启日志功能IOS的IPS支持syslog来发送事件通知,日志通知功能默认为开启状态,如果logging console是使能状态,可以看到IPS的sy
39、slog消息。如果日志SYSLOG没有使能,可以将其使能或说开启R1(config)# ip ips notify log根据需要,在特权模式下前往clock set命令设置时间等信息(xnx)。R1# clock set 01:20:00 6 january 2009检查路由器对于日志的timestamp service是否已经开启,可以用show run命令查看,如果时间戳服务没有开启要将其开启。R1(config)# service timestamps log datetime msec发送日志消息到日志服务器,Syslog server的IP地址为0R1(config)# loggi
40、ng host 0共三十七页附:配置(pizh)案例第六步:配置IOS的IPS所使用的signature类别使用retired true命令退订所有签名类(在signature库中的所有signatures将被释放掉)。使用retired false命令引用ios_ips基本signature。R1(config)# ip ips signature-categoryR1(config-ips-category)# category allR1(config-ips-category-action)# retired trueR1(config-ips-category-action)# ex
41、itR1(config-ips-category)# category ios_ips basicR1(config-ips-category-action)# retired falseR1(config-ips-category-action)# exitR1(config-ips-cateogry)# exitDo you want to accept these changes? confirm 第七步:应用IPS规则到接口上去应用IPS规则Rule到接口的命令是在接口模式下执行ip ips name direction命令。本任务中应用规则在到R1中由器的Fa0/0的出站outbound方向上。在开启IPS后,一些日志消息(xio xi)会被发送到命令行的控制台上,表明IPS引擎被初始化完成。注意:方向如果是IN,那么表示IPS只检查进入此接口的流量。同样,方向如果是OUT,那么表示IPS只检查从此接口流出的数据流量。R1(config)# interface fa0/0 R1(con
温馨提示
- 1. 本站所有资源如无特殊说明,都需要本地电脑安装OFFICE2007和PDF阅读器。图纸软件为CAD,CAXA,PROE,UG,SolidWorks等.压缩文件请下载最新的WinRAR软件解压。
- 2. 本站的文档不包含任何第三方提供的附件图纸等,如果需要附件,请联系上传者。文件的所有权益归上传用户所有。
- 3. 本站RAR压缩包中若带图纸,网页内容里面会有图纸预览,若没有图纸预览就没有图纸。
- 4. 未经权益所有人同意不得将文件中的内容挪作商业或盈利用途。
- 5. 人人文库网仅提供信息存储空间,仅对用户上传内容的表现方式做保护处理,对用户上传分享的文档内容本身不做任何修改或编辑,并不能对任何下载内容负责。
- 6. 下载文件中如有侵权或不适当内容,请与我们联系,我们立即纠正。
- 7. 本站不保证下载资源的准确性、安全性和完整性, 同时也不承担用户因使用这些下载资源对自己和他人造成任何形式的伤害或损失。
最新文档
- 2026年网络安全专家考试题集含网络攻击手段
- 2026年经济学原理市场与金融知识应用题集
- 2026年物流与供应链管理试题库及答案详解
- 2026年软件工程师面试编程题集
- 2026年工程结构设计与材料性能标准测试题目
- 语言策略在信任构建中的应用研究
- 基于WS-I的CORBA与Web服务标准化研究
- 2026年长春市环境工程师资格认证指南试卷及答案
- 税务师考试备考技巧分享试题及答案
- 城市与乡村绿化环保措施考试及答案
- 2026版离婚协议书(官方标准版)
- 2026届山东省济南市高三上学期第一次模拟考试物理试题(原卷+解析)
- 医患沟通学与医学的关系
- 洗浴中心服务规范与流程(标准版)
- 北京市怀柔区2026年国有企业管培生公开招聘21人考试题库必考题
- 2026年陕西财经职业技术学院单招职业技能测试题库参考答案详解
- 2026年区块链基础培训课件与可信数据应用场景指南
- 雨课堂学堂在线学堂云《课程与教学论( 华师)》单元测试考核答案
- 2025年豆制品千张销量及餐桌烹饪调研汇报
- 不良事件上报流程及处理
- 为老年人更换纸尿裤

评论
0/150
提交评论